What is CPTC?
If you are not around the scene of collegiate cyber competitions, you may not know what CPTC is. CPTC is the Collegiate Penetration Testing Competition. Unlike most traditional collegiate cyber competitions, CPTC aims to mimic the activities conducted during a real-world penetration testing engagement. In fact, the competition organizers themselves tend to push the narrative that CPTC is less of a competition and more of a realistic learning experience where students get to play the role of consultants where they must perform well both technically and non-technically. This means that a team can be super 1337 h4x0rs, but if they cannot communicate their findings to a client, their work is that of shambles and not valuable/impactful to the customer. This is the primary message the CPTC organizers emphasizes for students.
My Experience with CPTC
Since joining UTSA’s team as a freshman in 2022, I have grown a lot as a result of this competition. My favorite part about this competition is that it emphasizes non-technical job-ready skills to include presenting, report-writing, professional client-facing communication, and so much more while also being a highly technical competition as well. The skills I have developed through this competition have directly impacted my quality of work and have prepared me for the industry. I highly encourage anybody who is interested in penetration testing, or cybersecurity in general, to try this competition if you are given the chance. You will not regret it.
Okay, back to the competition..
How does it work?
Each year, volunteers and sponsors develop a mock organization that is seeking penetration testing services. Teams of up to 6 primary members (2 alternates, 8 maximum) from each school represent their own consulting firm providing this service for the mock organization. As in the real world, this mock organization sends out an RFP (Request for Proposal) outlining a description of their business, their specific needs, and some details about the type of security assessment they are looking for. With this, each team sends their proposal outlining an introduction of the team and their relevant credentials, a suitability for purpose, resumes, and contact information. Once the proposal submission deadline has past, the organization will select teams that will proceed to conduct an initial penetration test (regional round), and based on their performance, a re-test (Global Finals round).
Once teams are selected, the regional round is hosted. The list of regions and the respective dates are shown below:

Team Composition
Before moving onto the competition itself, let’s talk about team composition. UTSA has a very long history with collegiate cyber competitions, including the fact that we developed CCDC. In the past, there has not been a very selective process when it came to team composition since until a few years ago, only a few people dedicated themselves to these competitions. This, of course, has changed especially since our cybersecurity program has grown immensely. For the first time, students were competing for spots on teams, which is a good thing.
This year, our coach required that students complete HackTheBox machines/challenges, or other cyber-related challenges and submit write-ups to him and the team captain for a chance at a spot on the team. These write-ups would be evaluated by accuracy, effort, completeness, and writing skill. This was effective because it allowed our coach and team captain to determine the technical and professional capabilities of students in an objective manner. We also had meetings once a week leading up to team selection and the competition itself covering all sorts of penetration testing topics. Spots were also determined by attendance to these meetings. This wholly ensured that the final team consisted of students who were technically capable and had strong work ethic and time management skills. It also removed bias from the team selection since it was mostly based on objective assessment. This meant that anybody had a chance to compete so long as they could prove themselves.
After a long few months between late Summer and the beginning of the Fall semester, the team was finally selected and of course, I had another opportunity to compete with a great team this season.
Before moving forward, I want to take a moment to highlight our team members:

From left to right: Alex Bryant, Logan Goins, Alexis Obeng, Julian Peña (me 🙂), Benjamin Anderson (our coach), Aditya Dindi, Jacob Rahimi (team captain), and John Newsom (second coach + mentor + amazing person)
At the time of this writing, this team is definitely the closest to the “dream team” I could imagine.
Starting with Alex Bryant, he is a wiz with physical security and web app pentesting. His role on the team is primarily in leading web application tests and in the case of CPTC8 (2022-2023), he was the one to turn to when we needed to crack open a safe without special equipment.
Next up is Logan Goins. Within minutes after meeting Logan, I absolutely knew he had to be on our CPTC team. His grit, determination, and incredibly fast ability to learn new things absolutely sets him apart from the average freshman at UTSA and as a student/professional. Since meeting him, he has continued to develop his very own stage-0 C2 framework known as HeadHunter, in C which we have used in and out of CPTC. Furthermore, obtaining CompTIA Security+ and CySA+ in highschool was not enough for him. Shortly after joining the team, he embarked on his 90-day journey to earn the OSCP certification and passed on his first attempt. By the way, this made him 1 out of 3 OSCP-holders on our team (including myself and Aditya Dindi). I could go on a super long tangent talking about how great Logan is, but you can read more about him and his adventures at his blog. Overall, I am incredibly grateful to have him on our team.
Moving on, we have our wonderful Alexis Obeng. I had the opportunity to meet Alexis prior to her enrolling at UTSA in the CyberPatriot competition and continued to work with her during our internship at Booz Allen Hamilton. Alexis has a high spirit and is always eager to learn. Having the opportunity to mentor her and watch her grow since our internship and experience with CPTC has been very rewarding. She has made great contributions to our team including technical documentation, organization, and a breadth of knowledge with AWS penetration testing. We all love having her on our team and I look forward to the incredible things she will continue to do in CPTC and at UTSA.
Under the left tusk, we have Aditya Dindi. Aditya is very enthusiastic about this stuff and was the second person in UTSA CPTC history to obtain OSCP. Being a jack of many trades, Aditya is a great asset on our team and is able to handle a variety of tasks at once. He has also been a great mentor for our entire team, teaching many lessons during our meetings. He also loves One Piece. Ask him about it 😉.
Last, but DEFINITELY not least, our team captain, Jacob Rahimi. I have known Jacob since my highschool days competing in CyberPatriot. Over the years, he has been a great leadership figure and by far exemplifies all the right qualities of a great team captain. Out of all of us, he has the most variety when it comes to technical abilities, professional communication, and project management. All of these things make him an outstanding leader. Did I also mention he is a MASTER at everything MS Office-related? No? Ask him about this funny symbol and you’ll find out:

war (report writing) flashbacks intensify
Alongside leading our entire team and handling everything technical and administrative, he has spearheaded and innovated our report-writing procedures and other professional documentation. Much credit is due to him for our success and we are all very grateful to have him.
CPTC9 Theme
Every year, the CPTC organizers come up with a fictitious organization seeking pentesting services. This year, the theme was an airport named after the father of Bob Kalka, Global Leader of Information Security at IBM: The Robert A. Kalka Metropolitan Skyport (RAKMS).

Preparing for Competition - Stage 1: Technical
With an incredible team assembled, it was time to get down to business. With a few of us being returning competitors, we knew what to expect and immediately got to work. Meeting once a week before regionals, we all took turns leading hands-on lessons on topics such as Active Directory Attacks, IoT/SCADA, Web/API, OSINT, Report Writing, Presenting, etc. These lessons would be carried out by utilizing public resources such as HackTheBox or TryHackMe and occasionally hand-made for our team.
Be careful when you are pentesting OT infra….
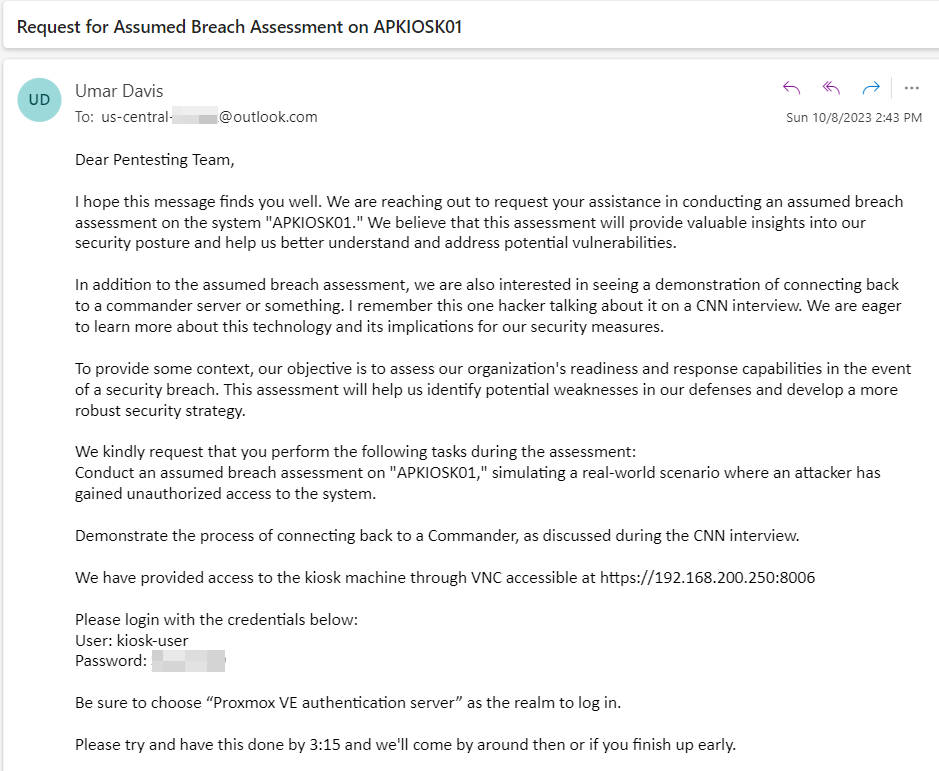
Assumed Breach inject during mock competition
During each of our lessons, we strived to apply our newly-found skills to the competition. It takes a lot to succeed in this competition and we knew that, so we worked hard to do well.
Preparing for Competition - Stage 2: Tooling
Every pentesting team needs tools to get the job done and this is something we happen to know very well. There are many ways to accomplish the same task and tools can usually speed up these tasks. One of the most time-consuming and stressful parts of the competition is the deliverable: a professional penetration test report.
The tool we used for reporting was SpecterOps’ very own GhostWriter.
GhostWriter is a tool that makes reporting on pentest and red team engagements much easier. Its collaborative web-based platform makes it easy for teams to manage several projects, organize findings, logs, and much more all at once. One of my favorite Ghostwriter features is its integration with the Jinja2 templating engine which allowed us to create and import a report template and let Ghostwriter insert all of our information.
With a single click of a button, we could turn this:
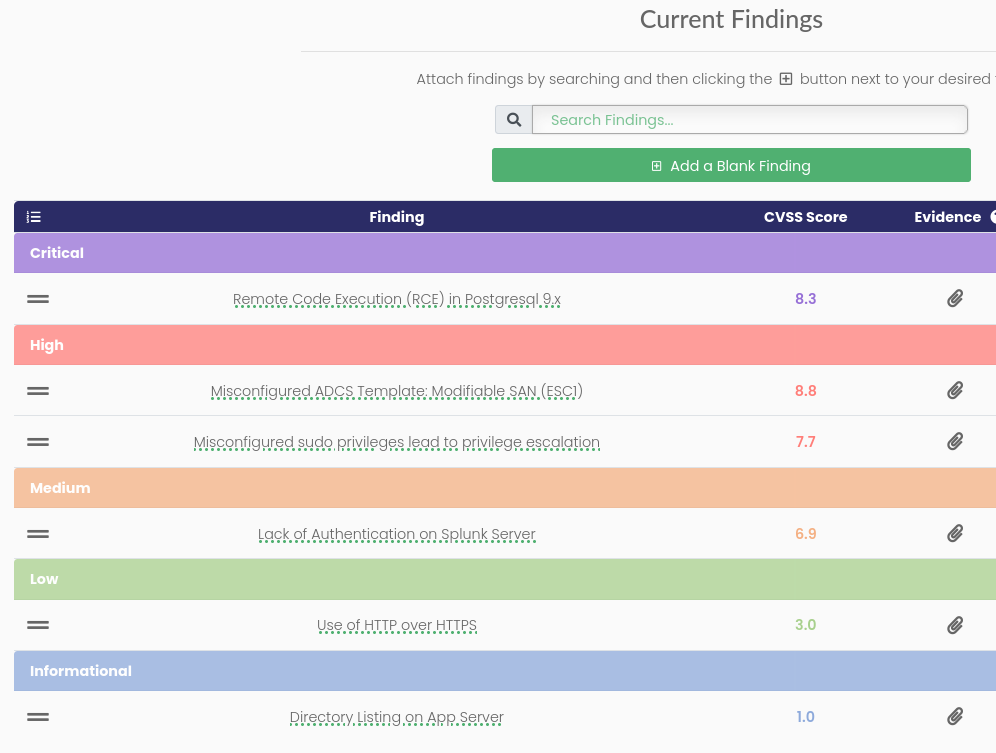
into this:
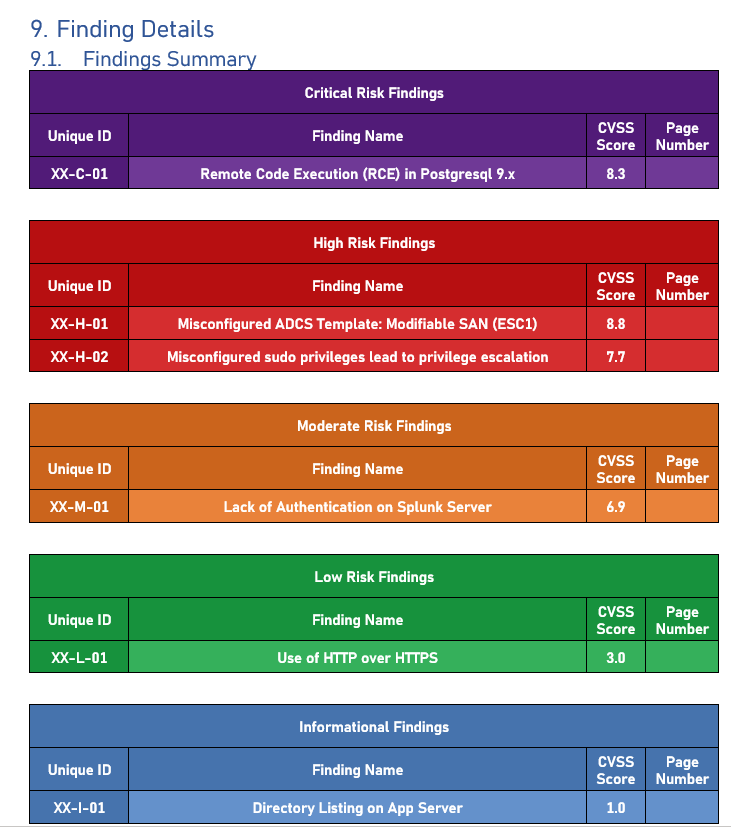
Findings summary auto completed with Ghostwriter
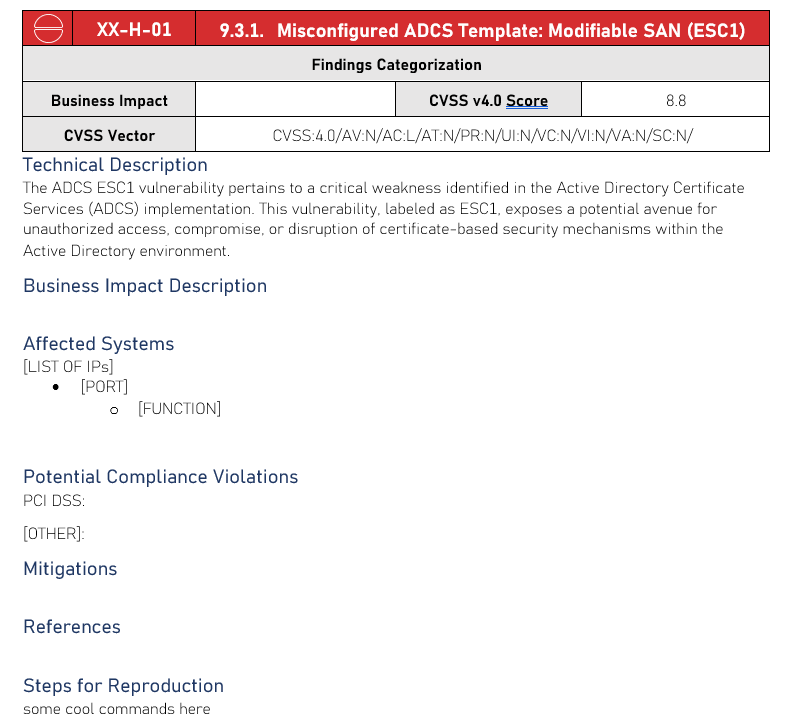
Sample finding created directly with Ghostwriter
I could write a whole blog about using Ghostwriter (and I might), but if you would like to learn more about it, I highly encourage you to watch Christopher Maddalena’s talk and demo on it here
Furthermore, we know that we wanted to collaborate on the same compromised machines. For this, we wanted to use a C2 framework. We decided to use Sliver as it was lightweight, had flawless local/remote forwarding mechanisms, and working built-in SOCKS5 proxy support.
![]()
Originally, we wanted to use Mythic, but since our VMs only had 4 GB of RAM and 2 processor cores, we opted out since Mythic loves to eat RAM for lunch.
Preparing for Competition - Stage 3: Whose Slide is it Anyway?
Alongside hands-on lessons, we also had seemingly unrelated twists and turns to keep us on our toes and make us fearless by the time competition came. During CPTC8 Global Finals, EvilMog from IBM X-Force Red had us playing a game called “Whose Slide is it Anyway?” The game is simple. Someone creates a slide deck, usually one that is very confusing, potentially controversial, and always hilarious. Players must present this deck to an audience as if they prepared it. Players should remain serious as to avoid breaking character during the presentation. You wouldn’t want to melt down, stutter, or get stuck during an executive briefing now, would you? This game is all about improvisation and improving confidence when it comes to public speaking. This game is inspired by its equivalent version hosted at DEFCON and has had other spin-offs in shows such as Impractical Jokers.

CPTC8: Whose Slide is it Anyway?
We decided to create our own version of this as part of our practices….

Aditya discussing the Shadow Wizard Money Gang and how it relates to lebron’s legacy
Enter CPTC Regionals (Central)
On October 14th, 2023, we competed in the Central Regionals competition at Tennessee Tech. During this competition, we were given access to both Windows jumpboxes and dedicated Kali machines to perform our attacks from. Prior to the competition we were given the following scope:
- Corporate network: 10.0.0.0/24
- User Network: 10.0.1.0/24
- Train Network: 10.0.20.0/24
- Guest Network: 10.0.200.0/24
But… Regionals threw us a curve ball as they added another asset into scope:
- An entire AWS environment..
Before regionals, we had not practiced much with pentesting AWS, but fortunately one of our teammates, Alex, was able to take on the lead role for pentesting AWS. Here, we discovered many flaws in IAM roles and the use of Lambda functions (web applications specifically).
Besides the random curve ball we had, we were able to compromise the entirety of the corporate network and bits of the other networks with common exploits such as EternalBlue and some web-based attacks. We did not, however, feel comfortable with the number of findings we had. With only 12 findings in our report, we were worried that we would not even place at regionals. In CPTC8, we felt fairly confident and were able to place 2nd in the Southeastern region, just below the University of Central Florida (UCF), but this time we were not sure how the results would pan out. In fact, by the end of competition, I felt very much down about our performance despite my teammates encouraging our overall morale.
The following morning, we had a few opening remarks and a guest speaker talk, then the moment we were all waiting for: The Award Ceremony.
Despite all of our doubts, we were able to snag the first place spot, leaving us all in complete shock.

Regionals → Global Finals
With 1st place at Regionals under our belts, we had a guaranteed spot at the Global Finals competition hosted at RIT. With this, we knew that we had to immediately start preparing.
One of the first things we did was a debrief on Regionals, highlighting the areas we did well on and also where we struggled. We also started re-writing our findings from regionals and preparing a re-test checklist since we knew that we would have a similar environment at Globals and we needed to know what findings were remediated by the client going in. Furthermore, we also prepared a slide deck template since we knew that we would have to give a presentation briefing at Globals.
Also, speaking of presentations, we did a substantial amount of work on our presentation skills leading up to globals. The difficult part about the presentation portion of the competition is that you only have 10 minutes, which is not a lot of time if you are not keeping track. During last seasons’ global finals presentation, we were unfortunately stopped by the 10-minute timer alarm right at the end of our presentation, causing us to take a huge hit in our overall score. You can see that presentation here.
We were NOT going to let this happen again, so we made this practice mandatory, having it assigned as “homework.”
CPTC Homework? Ain’t no way… 💀
Yes, you read that right. Due to our failure to finish our presentation on-time during CPTC8, our team captain and coach harped on making presentation practice a required homework. In the last week leading up to Global Finals, we were uploading at least 2 recordings of our parts of the presentation per day.
Global Finals
After anxiously waiting, the Global Finals competition finally arrived. Once we were connected to our jumpboxes, we immediately ran our scans. This was when we hit our first roadblock: network segmentation. Since this was a recommendation we gave at regionals, RAKMS took our advice and implemented strong network ACLs to prevent us from scanning several systems across each subnet initially. These ACLs were eventually dropped to allow for more comprehensive scanning, but this surely left us struggling to get a foothold at first. At the time, the only system that was exposed in the corporate subnet was the MS Exchange server though we did not have luck attempting to use exploits such as ProxyShell and ProxyNotShell. Once network ACLs were dropped, we immediately consulted RAKMS to test EternalBlue (MS17-010), only to find out that it was patched.
With limited options available to get back into the corporate network, we decided to use a well-known exploit called “ZeroLogon” (CVE-2020-1472). This is where the fun really began… This time, unfortunately, we did not consult RAKMS prior to executing the Zerologon attack against the corporate Domain Controller. This was our first mistake. While Zerologon provided us with a quick win, we failed to realize the implications of running the exploit.

Zerologon exploits a flaw in the implementation of the ComputeNetlogonCredential call of the Netlogon Remote Protocol (MS-NRPC) that allows an unauthenticated user to spoof the identity of the domain controller and set the Domain Controller’s machine account password to an empty one. Doing this allows an attacker effectively escalate their privileges to Domain Admin, but it comes at a serious cost - domain functionality. Changing the Domain Controller’s machine account password completely disrupts its ability to communicate with other systems in the domain until it is restored. Unfortunately, we had oversight in this critical detail and did NOT restore the machine account password. This led to a VERY angry knock at our door where the RAKMS Monitoring and IT staff questioned what we were doing and why we did not consult them prior to running this particular exploit. We learned a very valuable lesson here and I am SOOOOOOOOOO glad we did it here as opposed to a real client in the real world. Major props to the CPTC organizers for implementing these “educational opportunities” in the competition so that we could learn better practices to take into our professional careers at a low-stakes competition.
Nonetheless, we were able to resolve the issue related to Zerologon, but it definitely came at a major point deduction. We were, however, able to leverage this exploit to assess the corporate network and move on with our assessment.
Throughout the rest of the competition, we discovered many more vulnerabilities involving the exploitation of the AWS environment via excessive IAM role assumption privileges and links between S3 buckets and Lambda roles. I will leave these out for now until final reports are officially released.
Conclusion
The final day of the Global Finals competition came and we wrapped up the competition with an executive briefing presentation outlining our findings and recommendations from our assessment.
Unfortunately did not place. We did, however, win some cool radios for having the best vishing call for one of the injects. Overall, I am very happy with how we did. We improved a lot since the last competition and we will only get better and I look forward to the next competition.